Optionally, it is possible to create a SCIM integration from Okta to Honeydew and to sync user profiles to Honeydew using the SCIM 2.0 protocol.
This is especially useful if you want users to be deactivated in Honeydew when they are deactivated in Okta.
This integration will require two applications to be registered in Okta: the OpenID Connect integration and the SCIM integration.
The same users and groups must be assigned to both.
Set up your identity provider (IdP)
Create the Honeydew app integration in Okta.
- Login to your Okta Admin Console
-
Go to Applications > Applications and then click Create App Integration.
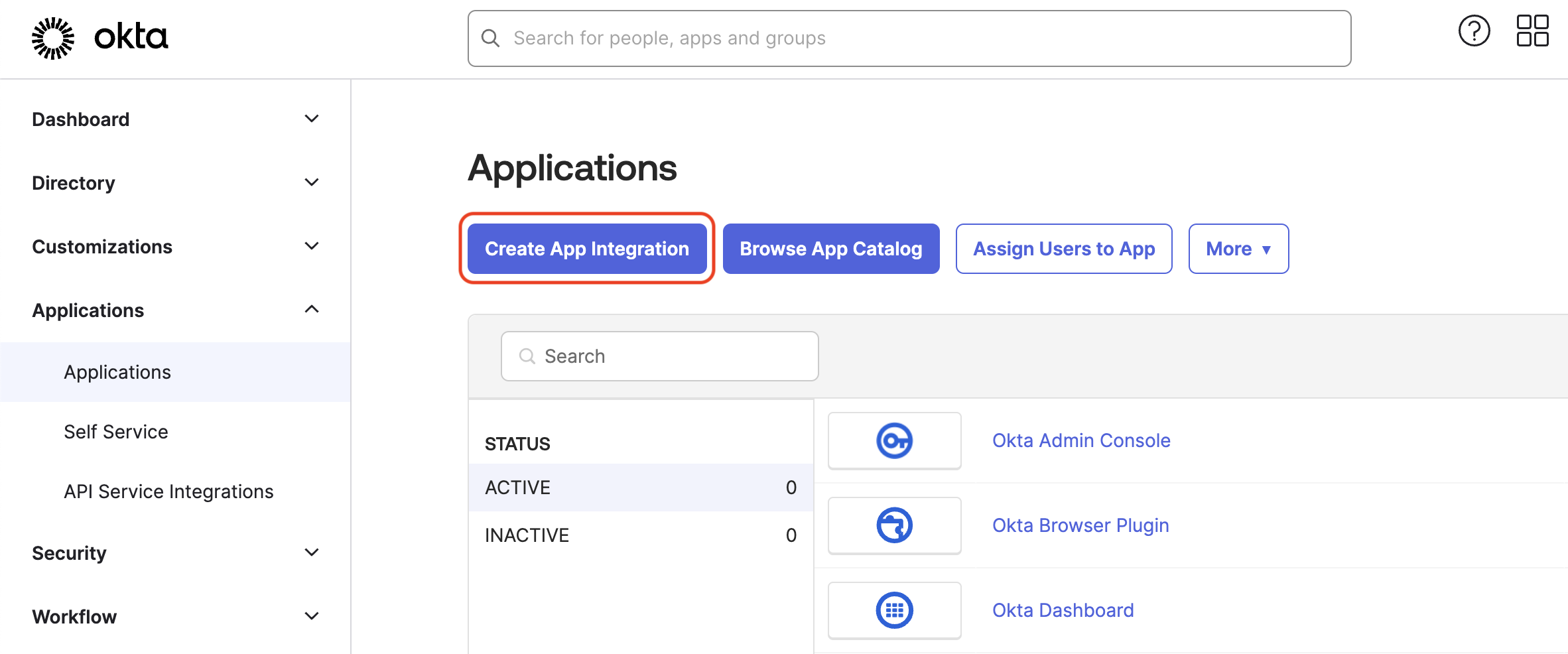
-
In the Create a new app integration dialog, choose OIDC - OpenID Connect as the Sign-in method.
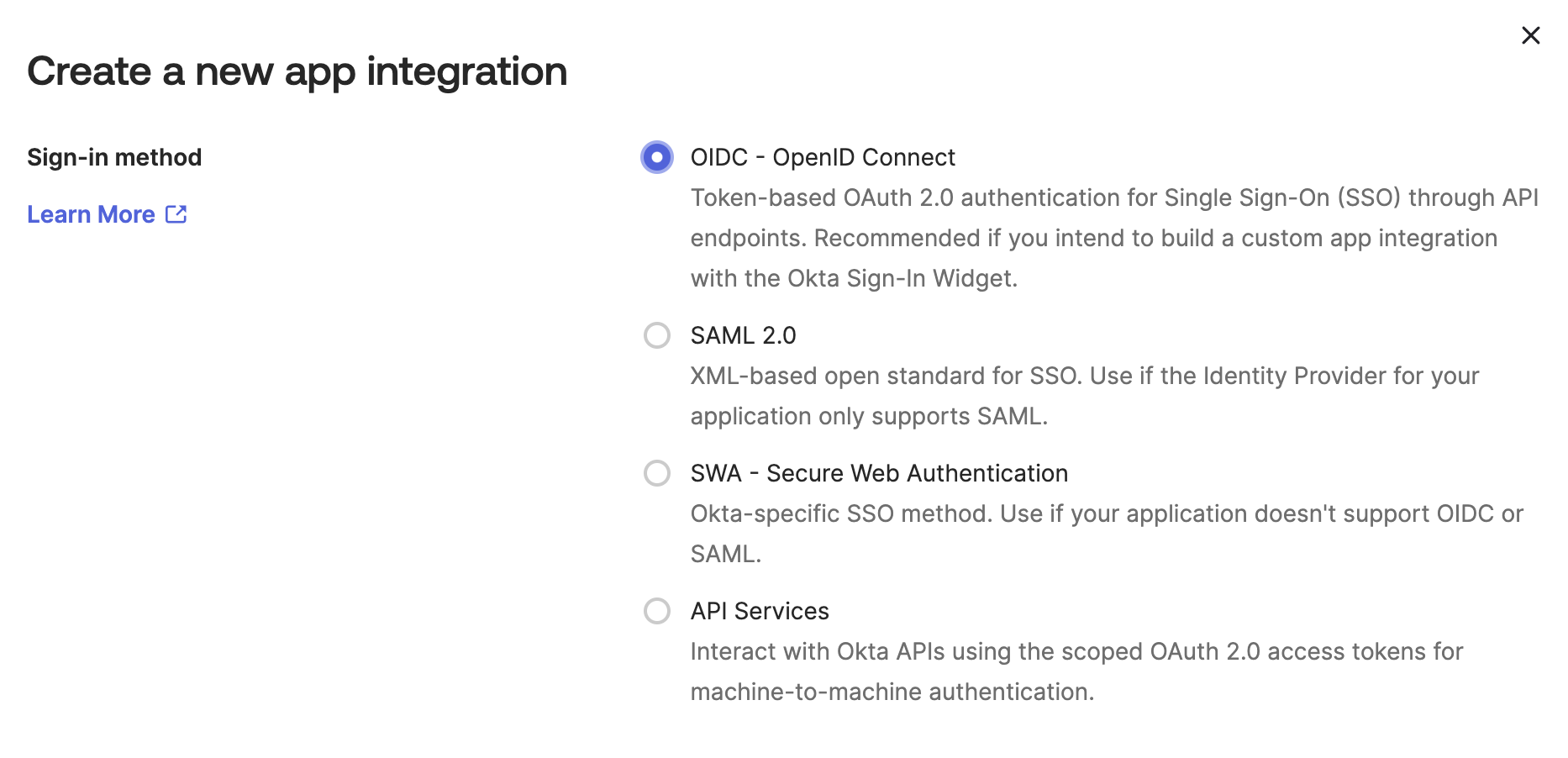
-
Choose Web Application as the Application type and click Next.
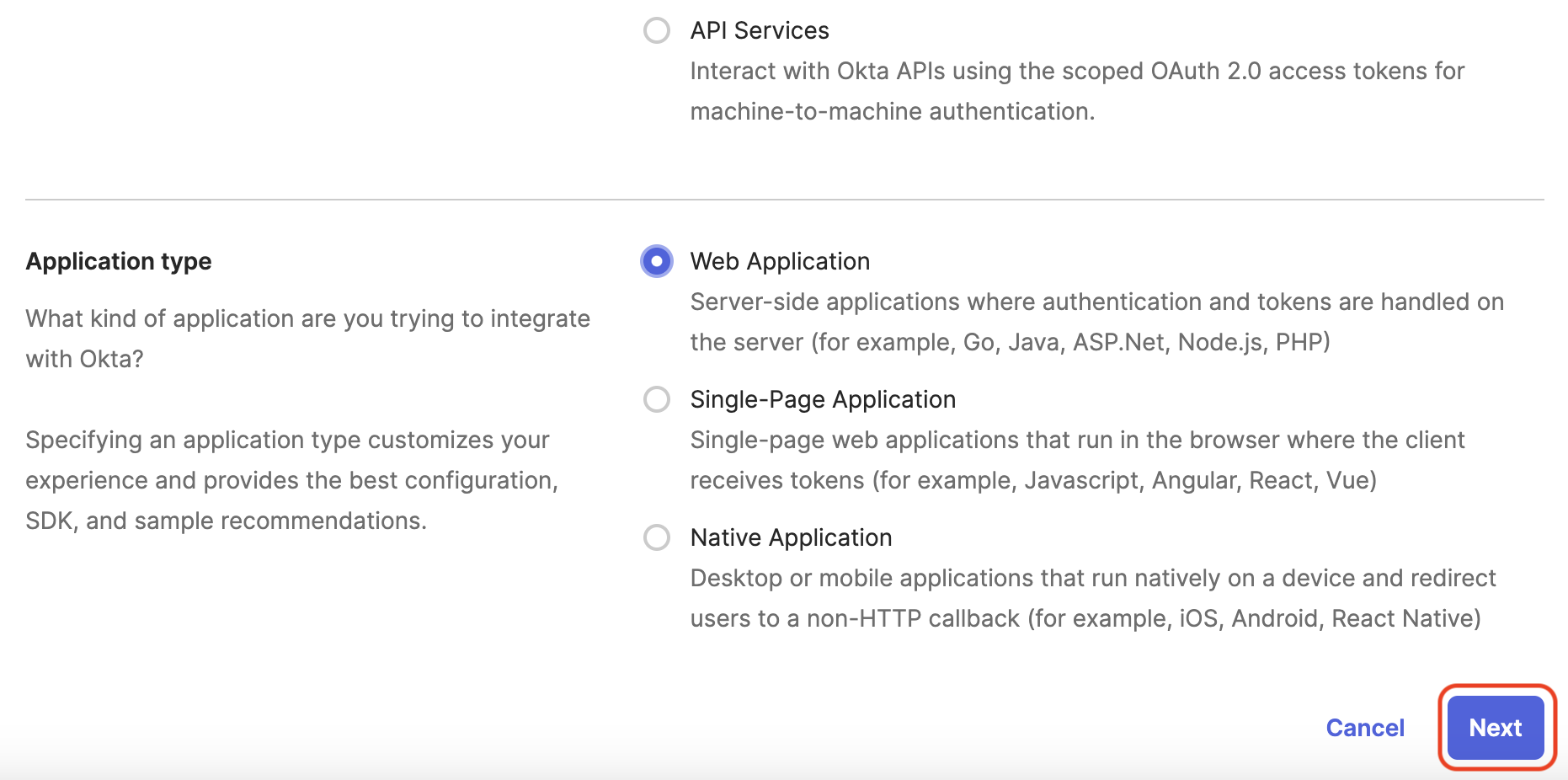
-
Choose a name for the app integration (e.g. Honeydew), and add an application icon (you can use the Honeydew
logo).
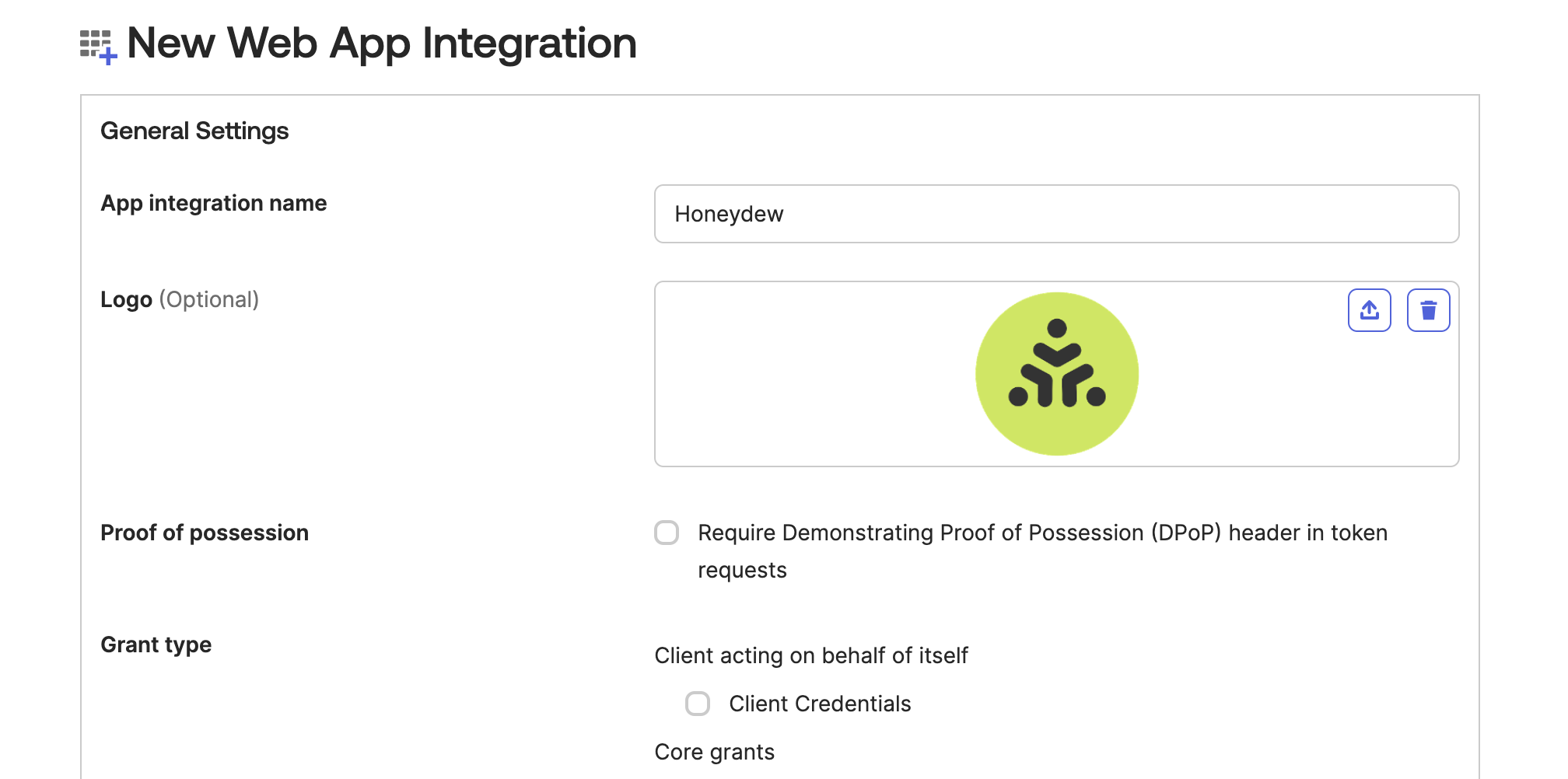
-
In the Sign-in redirect URIs field, add the following URI:
https://auth.honeydew.cloud/login/callback -
In the Sign-out redirect URIs field, add the following URI:
https://app.honeydew.cloud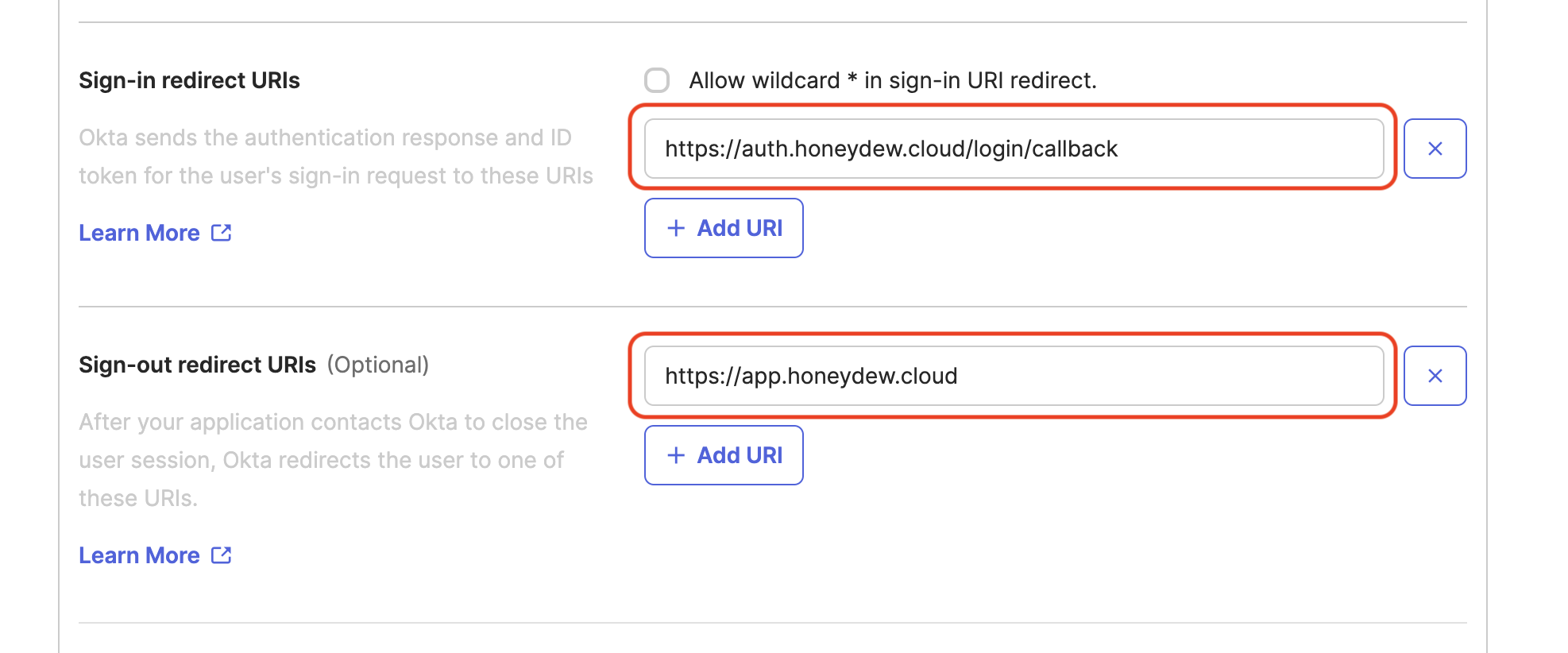
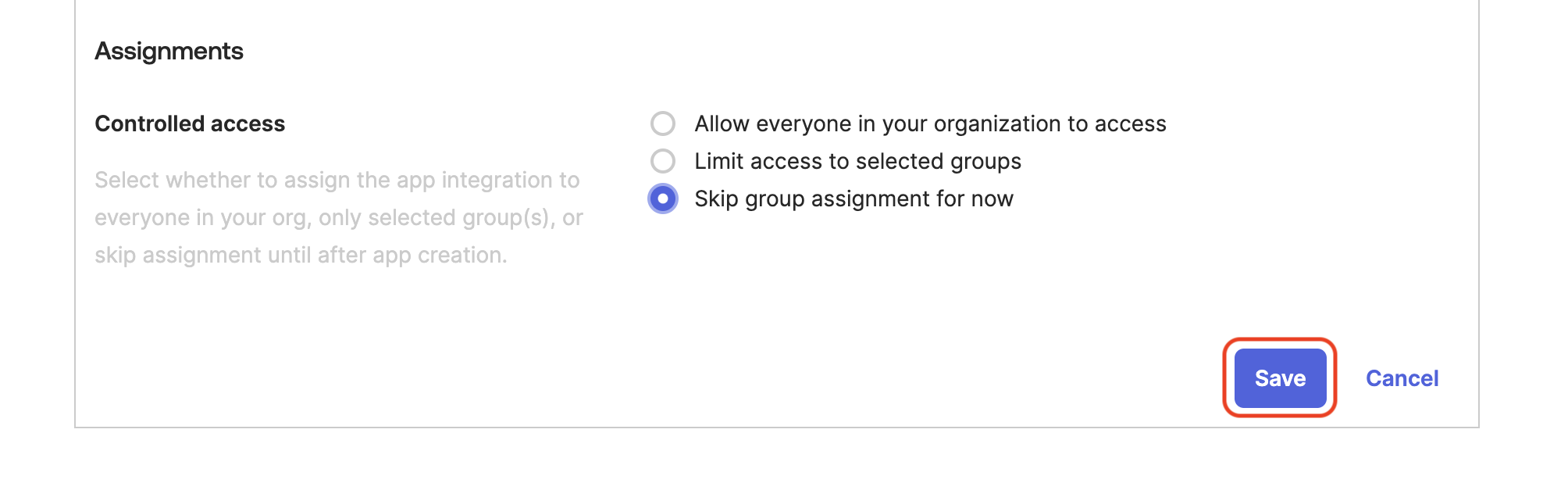
- In Assignments, choose the users or groups that will have access to the Honeydew app.
-
Click Save.
-
In the newly created app integration, and go to the General tab.
Save the following information as displayed in the General tab:
- Client ID (displayed in the Client Credentials section)
- Secret (displayed in the Client Secrets section, click Show to display the secret)
Configure Okta Integration in Honeydew
Now that we have our Okta app integration ready, we need to configure it in Honeydew.Please pass the following information to your Honeydew contact or to support@honeydew.ai:
- Okta Domain: The domain used to access your Okta account (e.g.
mydomain.okta.com) - Client ID you have saved from the Okta app integration in the previous step
- Client Secret you have saved from the Okta app integration in the previous step
- Email domains used in your company’s email addresses
- Initiate login URI (something like
https://app.honeydew.cloud/login?connection=<dedicated connection name>)
- SCIM Endpoint URL
- SCIM Bearer Token (a long string of characters)
Finish Honeydew app integration configuration in Okta
- In Okta, go to Applications > Applications and select your application name. Select the General tab and click Edit.
-
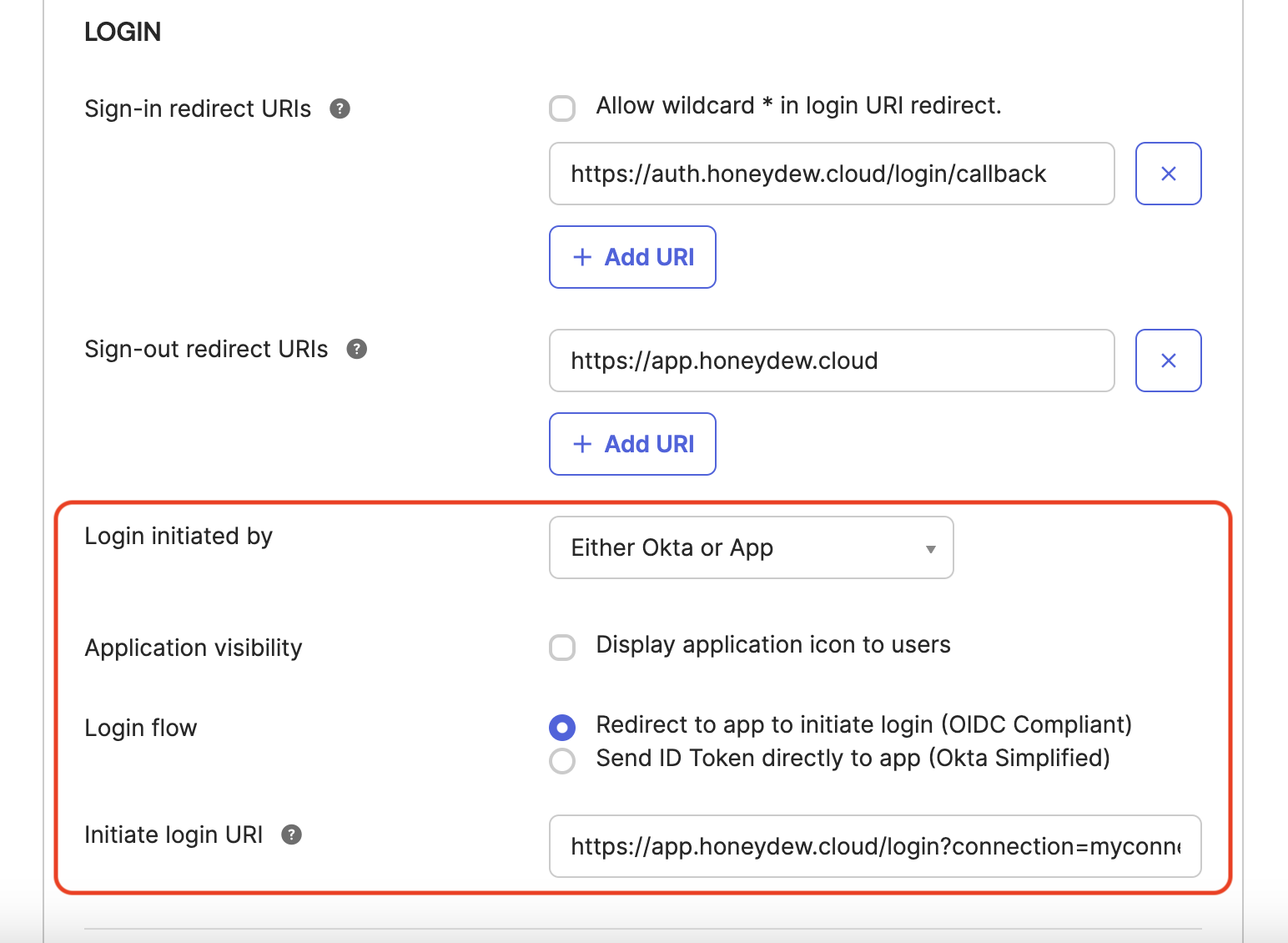
Scroll down to the Login section.
In the Login initiated by field, change the selection to Either Okta or App.
In Login flow, select Redirect to app to initiate login (OIDC compliant).
In Initiate login URI, add the URI you received from Honeydew.
- Scroll to the bottom of the Login section and click Save.
- Optionally, assign any users or groups that should have access to Honeydew.
- Once the configuration is complete, you can test the OIDC setup by logging in to Honeydew. Any user with an email address that matches the domain you provided will be able to log in using Okta. Upon login they will be redirected to the Okta login page.
Optional: Set up SCIM integration in Okta
The steps below are optional and only needed if you want to set up a SCIM integration from Okta to Honeydew.
You can find this documentation also here.
- Confirm that an OpenID Connect application has already been registered in the Okta Workforce tenant for OIDC-based user authentication.
- Confirm that your OpenID Connect application has disabled Federation Broker Mode.
- Register a second application in the Okta portal by selecting Applications > Applications, then choose Create App Integration, Secure Web Authentication, and Next.
- On the General App Settings page, set a name and a URL, then select Do not display application icon to users. The URL entered is not used in the SCIM integration.
- Select Finish.
- Navigate to the General tab, then choose Edit and go to the Provisioning section.
- Choose SCIM, then Save.
- Navigate to the integration’s Provisioning tab and then the Integration tab.
- Select Edit, then go to the SCIM connector base URL section and enter the SCIM Endpoint URL value you were provided by Honeydew.
- For Unique identifier field for users, enter userName.
- Under Supported provisioning actions, select Push New Users and Push Profile Updates, then choose HTTP Header as the Authentication Mode.
- Paste the token value into the Authorization field, picking Test Connection Configuration if you want to test the connection. Choose Save.
- Browse to Provisioning > Settings > To App and choose Edit.
- Enable Create Users, Update User Attributes, and Deactivate users. Choose Save.
-
Under the Attribute Mappings section, use the X button to delete the following lines, which are not needed and may cause issues during PUT operations:
Attribute Value Primary email type (user.email != null && user.email != '') ? 'work' : ''Primary phone type (user.primaryPhone != null && user.primaryPhone != '') ? 'work' : ''Address type (user.streetAddress != null && user.streetAddress != '') ? 'work' : '' - Use the Attribute Mappings section to configure any additional SCIM attributes you want Okta WIC to send to your SCIM endpoint. If you add custom attributes, they must include a valid SCIM 2.0 external namespace property. For more information on external namespaces, read Okta’s help section.
- You can now test user provisioning in the Assignments tab and test update operations by editing the user attributes in the Directory > People section of your Okta admin portal.